常用關鍵字
Enterprise WVPN
Wireless VPN (Wireless Virtual Private Network) is a secure 4G / HSDPA service targeting enterprises.
It uses standard IPSEC/MPLS network safety protocols to establish a exclusive WVPN network between the enterprise account and FET. It connects mobile workers and FET offices, providing a secure and reliable wireless network service. The user does not need install other soft wares nor set complicated settings. It is convenient and simple.
With WVPN, mobile workers can use various end devices to securely connect to the company’s internal information system via the exclusive enterprise WVPN channel anytime and anywhere to undergo various tasks.
Service Architecture
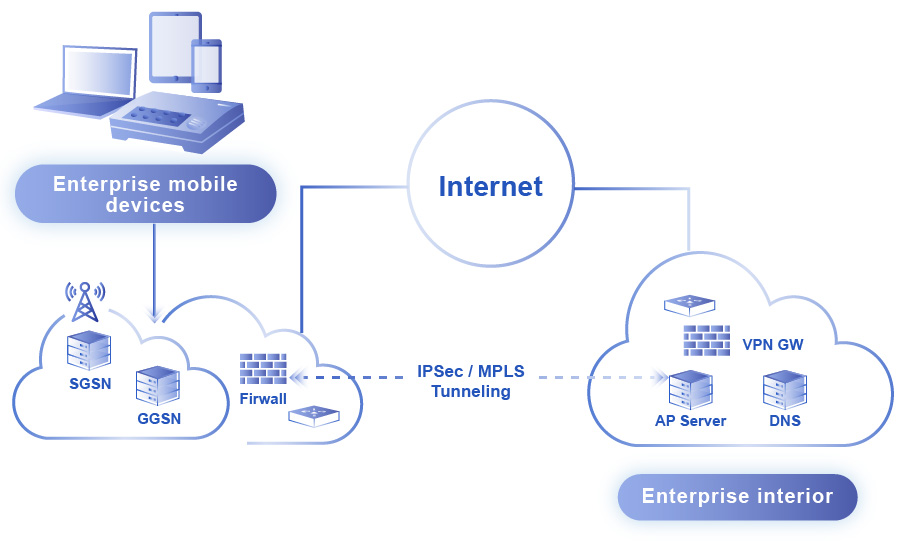
Service Features
Enterprise client exclusive VPN network, all data are encrypted/decrypted via IPSEC/MPLS, secure and reliable.
No complicated settings, simple controls, just like going online.
Exclusive APN to connect directly to the enterprise’s internal network. Customizable based on the network management requirements of the enterprise, specify specific network segments, and allocate dynamic or fixed IP.
With FET’s 4G coverage in Taiwan and international roaming services, remotely process company data and respond emails to greatly enhance employee productivity anywhere and anytime.
Security Mechanism
- Client can choose a name, but cannot be the same as an existing APN. Letters and numbers can be used, the first character cannot be a number.
- Ensures data confidentiality
- Prevents others from “eavesdropping” on the contents
- Ensures that the transmitted contents are not changed or damaged. Upholds data integrity
- Data source authentication, ensures data is not forged from third parties in the public network
- "Access Control List" mechanism
- Specific IP addresses can also be issued to each mobile number.
Contact us, we'll provide you the solution fits your needs





